by | Ahmad Razif Mohamad, razif@might.org.my | Natrah Mohd Emran, natrah@might.org.my
Online advertisers have a rather uncanny ability to steal your time with attention grabbing advertisements. Just as internet users go about their daily business online, oftentimes, users come across promo pop-ups that mirror their previous searches with ads that appeal to their individual interests. To the bemusement of many, it may only appear as an unwelcomed feature of the internet browser keeping track of their online activities. However, out of sight, users are unknowingly exposed to rampant data brokering activities that are threatening to imperil the integrity of consent given and are now becoming a heightened cause for security concern.
Look up personal data and privacy issues on Google, Cambridge Analytics and Facebook scandals are more than likely to populate your search results. Why is this significant? In the past, personal data had been exploited to achieve devastating results—distorting perceptions and in large measures, swung the outcomes of big events in favour of certain high-profile individuals. Most recently, personal data was obtained without any consent and social media was used to influence the 58th American presidential election held on the 8th of November 2016.
Consequently, the vast majority of internet users were targeted with politically nuanced advertisements individually tailored to their dispositions in order to manipulate decisions and vote for Donald Trump in the previous 2016 election. This was then mooted as a ‘psychological profiling and information warfare’. To an idea of the devastating effects of this modern warfare by simply going over some numbers, digest this; at the end of 2018’s first quarter, Facebook had 2.19 billion monthly active users.
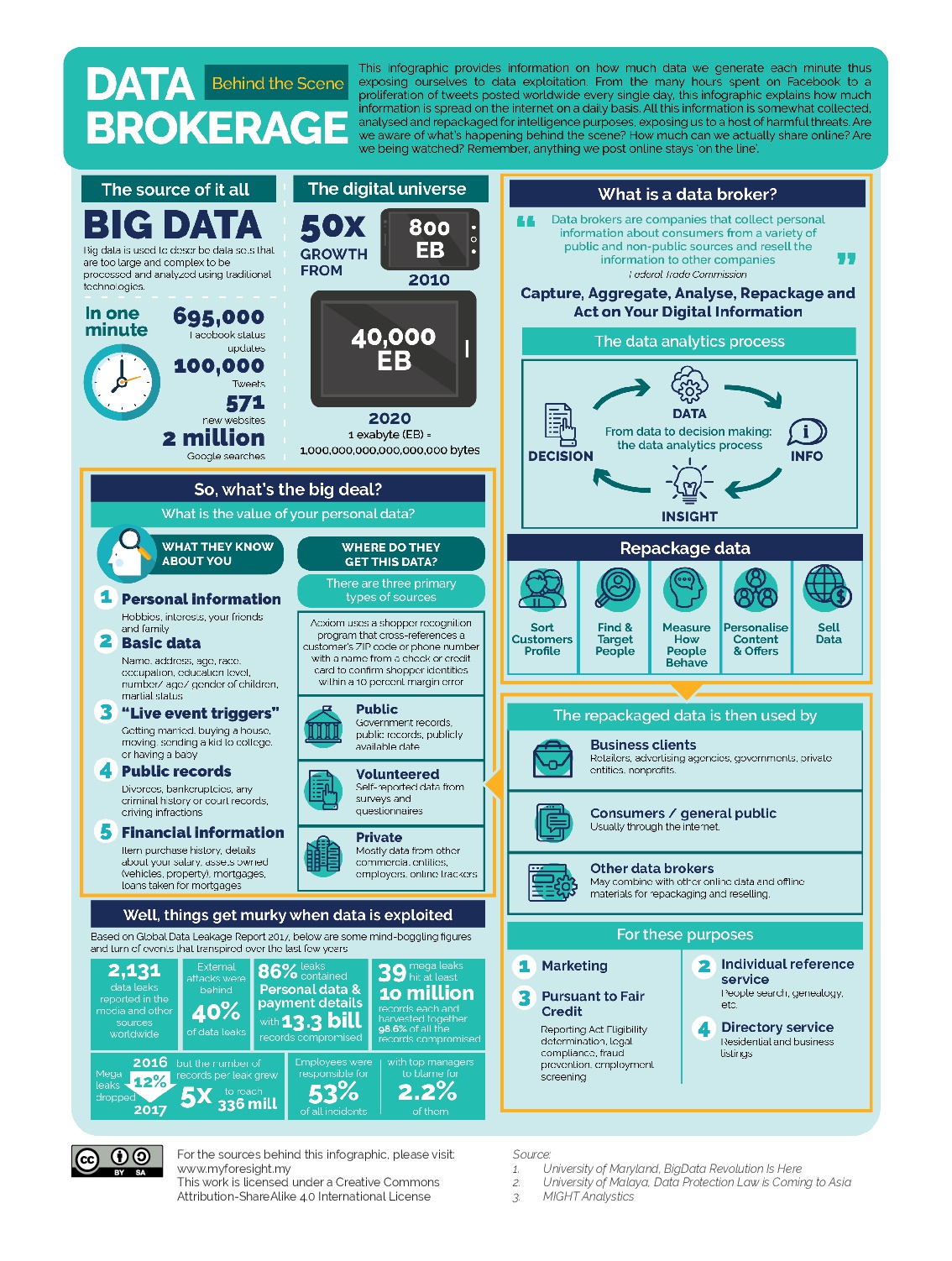
On the surface, we may only see or hear a glimpse of what is happening. Behind the scene however, numerous individuals and organisations are retrieving users’ personal information—subsequently packaging the data into specific profiles to be sold for huge amounts to large corporations. Thus, many experts have earmarked data as oil, in that it is unrefined and data brokers as, well, oil miners. Big data as it is more commonly known now, is a ‘smart’ commodity of high value that can be analysed computationally to reveal patterns, trends, and associations, especially relating to human behaviour and interactions. This is the driving factor of this unfettered yet highly profitable activity. And the unsettling issue we face at hand is not so much about what users share, but rather it concerns our personal data being collected and sold—apart for the unscrupulous gain of others, quite possibly misappropriation that may cause harm.
Case study 1
In Q3 2017, credit reporting agency Equifax lost $87.5 million when mitigating the consequences of a personal data leak hitting 145+ million people. As per its Q3 2017 financial statements, the company spent $55.5 million in direct costs, $17.1 million in incident response and professional fees, and $14.9 million in customer compensations. Equifax management expects additional costs of $56 million to $110 million in the coming months, apart from classaction lawsuits brewing in many U.S. states
Source: bleepingcomputer.com
Case study 2
A 28-year-old Indian woman working for a bank in UAE as a sales executive abused her position to log on to the e-system and extract data pertaining to as many as 2,500 InfoWatch Analytics Center Global Data Leakage Report, 2017 11 clients, including names, dates of birth, account balances, and bank card numbers, and then handed these data over to her Indian accomplice. As a result, the criminals managed to steal approximately $300,000 from bank accounts.
Source: khaleejtimes.com
Case study 3
In October 2017, a massive data leakage was published for sale on a well-known Malaysian online forum, Lowyat.Net. Because the forum posted sample data leaks, it triggered thousands of users’ anger as many were able to find their details leaked. The leakage dates back to 2012 to 2015. The data is a large list from Malaysian telcos, including Celcom, Maxis, Digi, Altel, Enabling Asia, FriendiMobile, MerchantTradeAsia, PLDT, RedTone, TuneTalk, UMobile and XOX. This could be the biggest data breach ever in Malaysian history. If this data falls into the wrong hands, it might enable other criminal activities, such as scam, phishing and targeted attacks to expand their targets. An estimated 50 million records were leaked and put up for sale.
Data brokers and marketers
In this era of pervasive networks, data brokers are a group who take stock and create value from collecting and selling your individual data. This contextual data is then sold to marketers who are always hunting for information about users and patterns to generate leads. Although these brokers have no relationships with the users, users’ personal data is being collected anonymously without them having any knowledge of it. Call it inappropriate, regardless, the growth in the so called business-intelligence tools sector has spawned a new market and created high demands for users’ personal data.
A growing concern
Needless to say, data brokers have largely contributed to this unhealthy epidemic and the unseemly growth of this market activity. In spite of typical broker activities (i.e., providing risk advice and facilitating insurance placement) brokers are the market makers in emerging risk threats and classes such as cyber security where little or no actuarial data actually exists. While a dash of creativity is certainly needed to develop new innovative promotions and solutions, many of these opportunistic brokers whom having identified this lucrative opportunity, invested heavily in data collection tools and technologies. These tools are then deployed to gather a greater understanding of both their own and users’ individual datasets to accelerate market growth.
While in many ways, there appears to be nothing malicious about this rather unsuspecting activity, it is the third party access to personal data that is causing the real concern. Although the buying, selling and aggregation of data may be largely hidden or whether this is just another market innovation, users can ill-afford to allow their personal data to be used beyond the stated or implied purpose when consent was given at the time of data collection. This is particularly interesting given that every second, users disclose a raft of information to the ‘supposedly’ trusted party when they agree to the terms and conditions that contain a clause authorising such sharing of data. However, to construe user consent loosely or to exploit it without any regard for compliance as far as personal data privacy is concerned is just plain rash on the part of data brokers and marketers. With long-simmering concerns about data protection and the issue of trust chiefly hanging over unresolved, it makes perfect sense why lawmakers are currently mulling over tighter legislation to curb rampant personal data manipulation activities.
A concerted effort
Constantly evolving landscapes pertaining to data privacy rights, cyber threat capabilities, regional economics and political interests are giving rise to a number of possible scenarios. Meanwhile, contrast these scenarios and they will inevitably call for the implementation of a robust data privacy regime that requires better data management and security measures. Now, individuals and organisations must anticipate how data collection, the use of data, and transfer restrictions are likely to change over time. Therefore, to prevent any sight of harm, data privacy and security programs must be designed to respond to these changes faster than these covert market activities, hidden in plain sight possibly could.
In contrast to security vulnerabilities, data protection refers to practices and regulations designed to protect your personal information and ensure that you remain in control of it. Users are given total ownership of their own data and in every respect, users autonomously decide what they do with it or the party collecting it can do with it (e.g., sharing of data, access to data, duration of data storage, stated and implied purposes & permission to modify the data.)
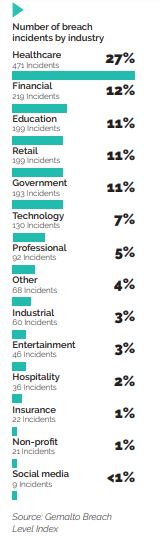
Standing still in the face of this situation however are various parties that are impacted by the issue. Governments from across the globe are working hard to resolve the issue, for if undeterred—is a situation threatening to spiral out of control. A heightened security interest is needed to ensure better protection of personal data. For example, in 2015, 21.5 million records were stolen from the US Office of Personnel Management. This stolen data contained highly sensitive personal data of federal employees and their family members. This type of attack is happening more frequently and actions should be taken to better protect individuals’ data information with a comprehensive data protection framework.
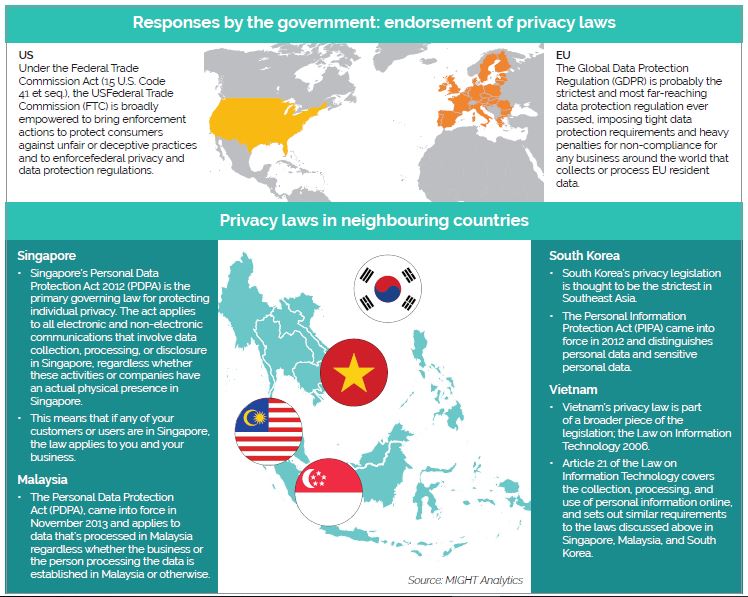
Increasingly, a number of technologies and trends have since caught up to address modern backup and data protection concerns. However, data protection technologies are not the one-size-fitsall solution users and organisations are so desperately seeking to deal with the multi-faceted data privacy issues and security threats. Whether we are dealing with ransom ware, big data, security or compliance issues, it differs for everyone, thus rendering the issue even more complex to be dealt with with just a single generic solution.
Just as technology can be used to automate data collection and processing, similarly, the myriad ways it can be seamlessly or covertly used to automate individual control over personal information can result in grave consequences. In light of this, the National Telecommunications and Information Administration, United States Department of Commerce Authentication, enlisted a specific criteria of technology to safeguard self-regulatory privacy regimes. While the technology can be used to protect personal privacy on the Internet, it also allows individuals to reap the benefits of customised services and convenient payment mechanisms.
In addition, these technologies can be used to build applications that minimise the need to reveal personal information and empower individuals to control the personal information they reveal and better understand how it will be used.

Final say—better stewardship
These are changing times. The boundaries between right and wrong are continually in flux. Across the board, users want better personal data supervision and sensible regulations that protect their interests, adequately. Essentially, users need to trust that information shared will be well supervised. Good supervision means that data will be used for the purposes allowed—and only for those purposes, restricting its use for only well comprehended applications, without murky disclaimers that don’t tell the whole story. In all cases, regardless of the process by which permission is obtained, supervision of data in fostering trust remains paramount. Finally, better codes of conduct and a compliance standard need to be embedded into brokers’ operations. Currently however, companies that collect data must work to establish greater trust and further mitigate the risks of harm.
With this in mind, what if in the future, users are allowed to sell their personal data as a source of income?
References:
1. Data protection technologies changing the market (Access on July 2018) https://searchdatabackup.
techtarget.com/essentialguide/Data-protection-technologies-changing-the-market
2. Data protection: why it matters and how to protect it (Access on July 2018) https://www.accessnow.
org/data-protection-matters-protect/
3. Zeyi Lin (2018), “Success Is Invisible, But Failure Is Public”1: Examining The U.S. Office of Personnel
Management Data Records Breach, (Access on August), https://repositories.lib.utexas.edu/
bitstream/handle/2152/65268/linzeyi_Thesis_Success%20Is%20Invisible,%20but%20Failure%20
is%20Public_2018.pdf?sequence=2
4. National Telecommunications and Information Administration, United States Department of
Commerce Authentication, “Chapter 5: Technology and Privacy Policy” (Access on August 2018),
https://www.ntia.doc.gov/page/chapter-5-technology-and-privacy-policy#5B
5. CyberSecurity Malaysia 2017, “2017 Data Breaches Known So Far”, e-Security | Vol: 43 – (2/2017),
(Access on August 2018), https://www.mycert.org.my/data/content_files/27/831.pdf